If you think you have identified a potential bug in the Ctrl Wallet Extension (Chrome web extension), Ctrl Mobile (iOS & Android apps) or in app.ctrl.xyz, please send an email to bugbounty@ctrl.xyz outlining the issue in sufficient detail. We will review your email, try to reproduce the issue and reply to you within 48 hours.
Ctrl Wallet Bug Bounty program
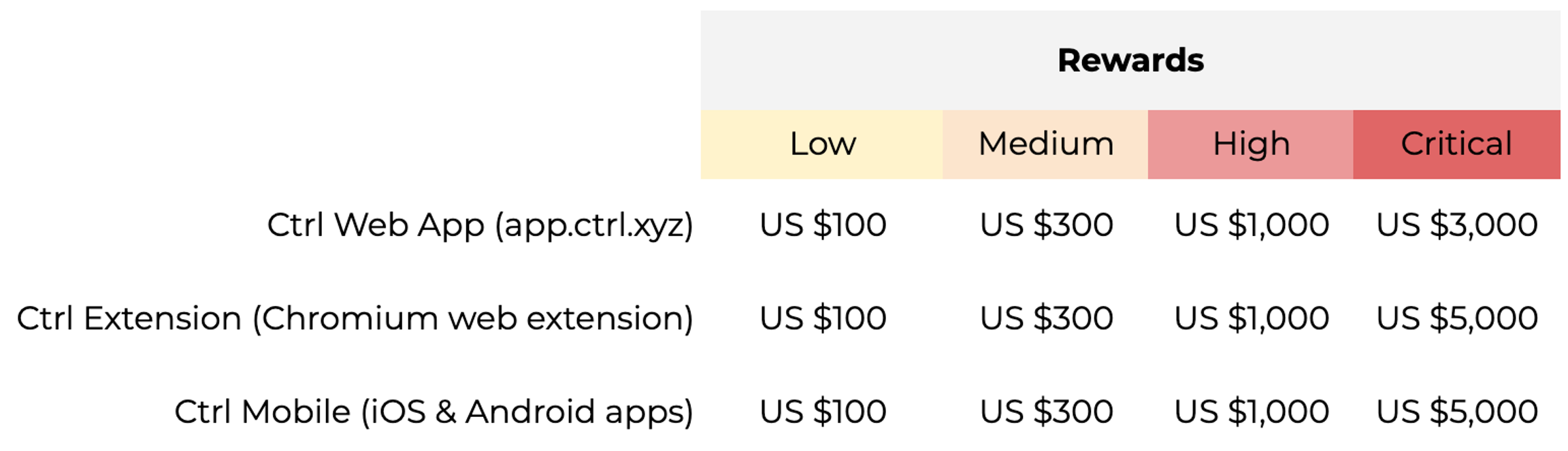
Rewards are based on severity per CVSS (Common Vulnerability Scoring Standard) and all reward decisions are at the sole discretion of Ctrl Ltd.
[Ctrl Wallet Bug Bounty Program was launched in May 2023. Last updated: February 2025]
Policy
Ctrl Ltd is delighted to be working with its community to find vulnerabilities in order to keep Ctrl Wallet and its users safe.
Ctrl Wallet is a non-custodial wallet that allows you to securely swap, store, and send crypto & NFTs across 2,300+ blockchains.
Response Targets
Ctrl Ltd will endeavour to meet the following SLAs (Service Level Agreements) for all bug reports that are submitted.
Response times:
- First Response: 48 hours
- Time to Triage: 2 business days
- Time to Bounty: 14 business days
- Time to Resolution: varies according to severity and complexity
Regular updates will be provided throughout the process.
Disclosure Policy
Please do not discuss any vulnerabilities (even resolved ones or potential ones) with anyone without the prior written consent of Ctrl Ltd.
Bug Bounty claim rules
Please provide detailed reports with clear, reproducible steps. If the report is not sufficiently clear or detailed for us to be able to reproduce the same issue, then it will not be eligible for a reward.
- Only submit one vulnerability per email (unless you need to chain or link vulnerabilities for impact).
- If we receive duplicated reports, we will only award the first report that was received (provided that it is sufficiently clear and detailed).
- Multiple vulnerabilities caused by one underlying issue will be awarded one bounty.
- Social engineering (e.g. phishing, smishing) is prohibited.
- Ensure that you avoid privacy violations, destruction of data, and interruption or degradation of Ctrl Wallet’s service.
- Only interact with accounts that you own (or where you have the account holder’s clear and express permission to do so).
Out of scope vulnerabilities
When reporting vulnerabilities, please consider (I) attack scenario / exploitability, and (II) security impact of the bug. The following issues are considered out of scope:
- Any activity that could lead to the disruption of our service (DoS).
- Clickjacking on pages with no sensitive actions.
- Cross-Site Request Forgery (CSRF) on unauthenticated forms or forms with no sensitive actions.
- Attacks requiring MITM or physical access to a user’s device.
- Previously known vulnerable libraries without a working Proof of Concept.
- Comma Separated Values (CSV) injection without demonstrating a vulnerability.
- Content spoofing and text injection issues without showing an attack vector and/or without being able to modify HTML/CSS.
- Rate limiting or bruteforce issues on non-authentication endpoints.
- Missing best practices in SSL/TLS configuration or in Content Security Policy.
- Missing email best practices (Invalid, incomplete or missing SPF/DKIM/DMARC records, etc.).
- Missing HttpOnly or Secure flags on cookies.
- Vulnerabilities only affecting users of outdated or unpatched browsers.
- Software version disclosure / Banner identification issues / Descriptive error messages or headers (e.g. stack traces, application or server errors).
- Public Zero-day vulnerabilities that have had an official patch for less than 1 month will be awarded on a case by case basis.
- Issues that require unlikely user interaction.
- Tabnabbing.
- Open redirect – unless an additional security impact can be demonstrated.
- ctrl.xyz website.
Thank you for helping to keep Ctrl Wallet and our users safe!
[Ctrl Wallet Bug Bounty Program was launched in May 2023. Last updated: February 2025]